SSH Tunneling Scenarios
Scenario 2 - Dynamic:
Using our first hop in to the network, we can keep using tools on our attack machine to enumerate the network further with dynamic port forwarding and using proxychains.
Create a tunnel to your port 9050 and logging in to Hop 1. By default proxychains uses port 9050 but can be configured in the /etc/proxychains.conf file on the attacking machine. By using dynamic forwarding, we can point to more than 1 port using a local or remote forward.
ssh -f -N -D 9050 root@Hop1
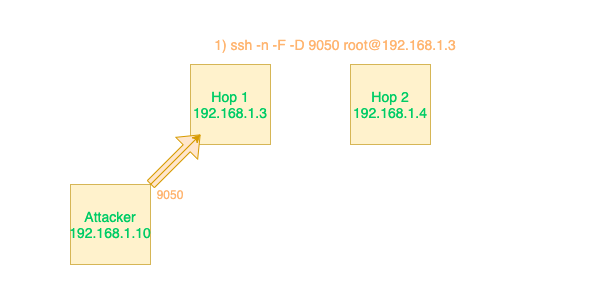
Now we can use proxychains to forward through the localhost:9050 port that is now open and tunneled through Hop1.
proxychains nmap -n -Pn -sT --top-ports 1000 Hop2

It is necessary to turn off UDP and ICMP protocols when using proxychains hence the -n (no DNS resolution), -Pn (disable ping), and -sT (TCP connect).
